Email is a vital part of our lives, both for business and personal communications. However, this integral tool is increasingly vulnerable to malicious attacks by cybercriminals aiming to steal credentials,…
Email is a vital part of our lives, both for business and personal communications. However, this integral tool is increasingly vulnerable to malicious attacks by cybercriminals aiming to steal credentials,…
As businesses move to digital transformation, Secure Access Service Edge (SASE) has emerged as a prevailing approach to securing vast networks and diverse endpoints. However, the right implementation of SASE…
This summer and fall, our team has written a great deal on how Juniper Networks’ intent-based networking (IBN) technology is helping companies automate the configuration, deployment, and management of enterprise…
As an industry, it can be argued that healthcare experienced the greatest number of technological challenges at the height of the pandemic. Identifying and implementing the technology that was required…
Security concerns are constant for every enterprise. More employees working from home (or anywhere, really) and other factors leads to network complexity and growth in the cost of data breaches….
Our review of 2021 IT trends reported that Zero Trust Network Access (ZTNA) was not only a common feature for enterprise IT teams, but that it will be sticking around…
Over the last decade, the topic of cybersecurity has shifted from being a technical subject to a mainstream topic impacting every facet of the organization. As cyberattacks become increasingly more…
Today’s cybercriminals are better equipped and are utilizing technology that’s more advanced by the day. With the value and importance of data only growing, protecting that data has never been…
As global industry evolves, digital innovation that features a hybrid, “from anywhere” business environment has become critical to modern workforces. New formats, like zero-trust access (ZTA), allow employees and external…
Regardless of the subject, there’s no one better to learn from than the experts. With this thought in mind, we recently held a cybersecurity webinar featuring Kevin Mitnick, a famous…
In the last six months, the fear of cyberattacks has grown significantly, largely due to several high-profile incidents that left enterprises struggling to deal with the fall out and the…
In the past year and a half, securely facilitating remote working has become a priority for a majority of enterprises. It’s also become clear that remote working is going to…
Even as enterprises put the chaos of 2020 behind them, cybersecurity holdovers from the past year continue to haunt IT security teams. In addition, new security threats rear their ugly…
As an IT leader, cybersecurity threats are constantly on your mind. They lurk in dark corners, lay in wait and when a moment of vulnerability presents itself, they strike! The…
Even as employees return to the office, just as many are choosing to stay remote. As a result, many enterprises need solutions that can provide specialized security for remote workforces….
Over the last year, the need to support employees from alternative working locations has risen dramatically. However, even as employees return to the office, when given the choice, many are…
IT security is an increasingly complex mission, especially after the turmoil of 2020. If your organization is like most, your workforce is likely still dispersed, your employees are utilizing their…
The greatest measure of an IT security solution, besides its usefulness in protecting the enterprise from threats, is how cost-effective it is. This is especially true in the eyes of…
When it comes to service delivery, there has never been more pressure on IT teams than today. With rapid adoption of digital technology and the prioritization of responsiveness, employees, customers,…
For IT, 2021 will be all about polishing and refining the strategies rapidly put in place to facilitate the employee exodus from the campus to the home. Remote workforces, once…
So we’re nearing the end of 2020, and luckily the shock and awe of the pandemic has largely worn off as employees have adjusted to the work from home life….
Whatever you need, we’ll make it work. Each Friday you can expect to see a new “Industry Info to Know” blog post from WEI consisting of a roundup of articles…
In part of one this two-part blog series, we discussed the recent study by Forrester Research outlining the economic impact of Macs in the enterprise. The study showed that while…
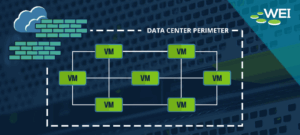
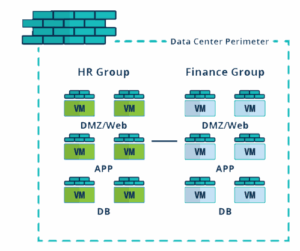
Data center architectures have continually evolved to meet the needs of mobile, social, big data, and cloud applications–and enterprise security solutions have evolved as well to support the new security…
With an increasing number of enterprises investing in digital transformation and the software defined data center (SDDC), IT leaders are getting accustomed to managing overwhelming large volumes of data and…
WEI is aware of the new vulnerabilities related to Intel and other CPUs which could potentially allow an attacker to gather privileged information from CPU cache and system memory, putting…
Regardless of organizational size or industry, every company faces significant data and network security concerns today. Those concerns increase substantially for organizations that deal with protected or sensitive information in…
Writer’s note: Every Thursday in November and December, this blog will highlight the SDN solution, Cisco ACI. As market acceptance and adoption increases for SDN, IT professionals can count on…
At WEI we are always looking for new and comprehensive solutions to meet our customers’ changing security needs. According to Symantec’s 2015 Internet Threat Report, the number of ransomware attacks…
Is your business utilizing data encryption in your security strategy? The process of changing information to make it unreadable to those except authorized users can help your company securely protect…