As enterprises push their digital transformation efforts into overdrive to support employees and make business decisions from anywhere, they open themselves up to a new world of data and security…
As enterprises push their digital transformation efforts into overdrive to support employees and make business decisions from anywhere, they open themselves up to a new world of data and security…
Unfortunately, as technology evolves, it’s not just the enterprise that benefits from the latest and greatest tools – so do the criminals who use them to attack businesses. With enterprises…
What is your enterprise’s cybersecurity process when it comes to ransomware preparedness? As a heavily relied upon technology leader, this is a critical question to ask yourself. Remember, there are…
In 2020, new IT Technologies emerged to drive change in response to the COVID-19 pandemic. As many enterprises shifted to a remote workforce, they were compelled to adapt to a…
Over the last decade, the topic of cybersecurity has shifted from being a technical subject to a mainstream topic impacting every facet of the organization. As cyberattacks become increasingly more…
Days after the attack on the Colonial Pipeline, MIT Sloan School of Management professor, Stuart Madnick, said in an interview, “I often say the worst is yet to come.” While…
Today’s cybercriminals are better equipped and are utilizing technology that’s more advanced by the day. With the value and importance of data only growing, protecting that data has never been…
As global industry evolves, digital innovation that features a hybrid, “from anywhere” business environment has become critical to modern workforces. New formats, like zero-trust access (ZTA), allow employees and external…
Regardless of the subject, there’s no one better to learn from than the experts. With this thought in mind, we recently held a cybersecurity webinar featuring Kevin Mitnick, a famous…
In the last six months, the fear of cyberattacks has grown significantly, largely due to several high-profile incidents that left enterprises struggling to deal with the fall out and the…
In the past year and a half, securely facilitating remote working has become a priority for a majority of enterprises. It’s also become clear that remote working is going to…
Even as enterprises put the chaos of 2020 behind them, cybersecurity holdovers from the past year continue to haunt IT security teams. In addition, new security threats rear their ugly…
As an IT leader, cybersecurity threats are constantly on your mind. They lurk in dark corners, lay in wait and when a moment of vulnerability presents itself, they strike! The…
Even as employees return to the office, just as many are choosing to stay remote. As a result, many enterprises need solutions that can provide specialized security for remote workforces….
Over the last year, the need to support employees from alternative working locations has risen dramatically. However, even as employees return to the office, when given the choice, many are…
The threat landscape is ever evolving, and today’s enterprises face more cybersecurity challenges than ever. Between the rise of cloud computing, increased utilization of internet of things (IoT) devices, and…
The greatest measure of an IT security solution, besides its usefulness in protecting the enterprise from threats, is how cost-effective it is. This is especially true in the eyes of…
Apple has a product to suit all aspects of your life with a platform that supports apps for your hobbies and entertainment, storage for your memorable photos and videos, and…
Whatever you need, we’ll make it work. Each Friday you can expect to see a new “Industry Info to Know” blog post from WEI consisting of a roundup of articles…
If your company is undergoing its digital transformation in order to achieve greater levels of agility, scalability, and efficiency, you may have realized the following correlation between size and security….
As enterprises modernize their IT infrastructure to meet evolving business demands the conversation of security is always top of mind. More and more companies are now managing a distributed enterprise,…
Mobile security is reaching a new era of stability and functionality, but watch out for these common mistakes that can threaten the efficiency of your EMM program. As businesses begin…
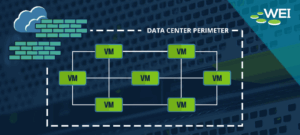
Data center architectures have continually evolved to meet the needs of mobile, social, big data, and cloud applications–and enterprise security solutions have evolved as well to support the new security…
With an increasing number of enterprises investing in digital transformation and the software defined data center (SDDC), IT leaders are getting accustomed to managing overwhelming large volumes of data and…
With the rise of digital transformation in today’s modern workplace, traditional Wide Area Network solutions are unable to keep up with enterprise demands. A growing number of organizations are moving…
With the expansion of the Internet of Things, the BYOD movement and emerging wireless technologies, you may be realizing its time to invest in a more modern approach to networking…
How much visibility do you have into your organization’s network? How confident is your IT team in its ability to accurately map out the network, which is a necessary step…
Are you considering switching your enterprise from a legacy hardware infrastructure to a more streamlined system? Are you afraid of the enterprise security risks that come with using a cloud-based…
WEI is aware of the new vulnerabilities related to Intel and other CPUs which could potentially allow an attacker to gather privileged information from CPU cache and system memory, putting…
In 2016, network security has been a topic of concern entering conversations in enterprise boardrooms across the world. With many recent high-profile hacks, security breaches and incidents of malware and…