Part 2 of WEI’s Cloud Security Foundations series. You can find part 1 here.
Setting up a secure AWS environment is a critical step for any organization looking to leverage the cloud effectively. However, without a solid security foundation, even the most advanced deployments can be vulnerable to costly misconfigurations and breaches.
According to recent industry reports, 80% of cloud security incidents stem from misconfigurations that could have been prevented with proper foundational controls. In the second edition of the three-part Cloud Security Foundation Series, we’ll walk you through a practical, five-phase roadmap to help you build and maintain a strong security posture in AWS from day one. To read revisit part one, click here.
Why Automation Matters: The Scale Challenge
Managing security across 5 AWS accounts manually? Challenging but doable. Managing security across 50+ accounts manually? Nearly impossible.
This is where AWS Control Tower and Organizations become game-changers. They transform security from a manual, error-prone process into an automated, scalable system that grows with your organization.
The Foundation: AWS Organizations + Control Tower Automation
Before diving into the phases, let’s discuss the automation backbone that enables everything else to be possible. AWS Control Tower is essentially an orchestration layer that sits on top of AWS Organizations, automating the setup and governance of your multi-account environment. Think of it as your security automation command center.
Why This Matters for Cybersecurity
AWS Organizations provides the basic multi-account structure and consolidated billing. Still, AWS Control Tower builds upon this by offering pre-configured security blueprints, service control policies (SCPs), and ongoing governance controls. The magic happens when these two services work together:
- Automated account provisioning through Account Factory with security guardrails baked in
- Centralized logging across all accounts with immutable log storage
- Preventive controls that stop risky configurations before they happen
- Detective controls that continuously monitor for drift and compliance violations
Phase 1: Establish Your Automated Landing Zone
| Goal | What “Good” Looks Like | AWS Services & Tools | Automation Layer |
| Multi-account governance | Separate prod, dev, shared-services, and security accounts | AWS Organizations, AWS Control Tower | Account Factory automation |
| Centralized, immutable logging | Org-wide CloudTrail into an S3 Log Archive account | CloudTrail, AWS Config, S3 Object Lock | Automatic log aggregation |
| Baseline guardrails | Prevent risky changes (e.g., public S3) | Control Tower preventive & detective guardrails | Policy enforcement automation |
| Self-service provisioning | Teams can create accounts with pre-approved security baselines | Account Factory, Service Catalog APIs | Template-driven provisioning |
Automation Deep Dive
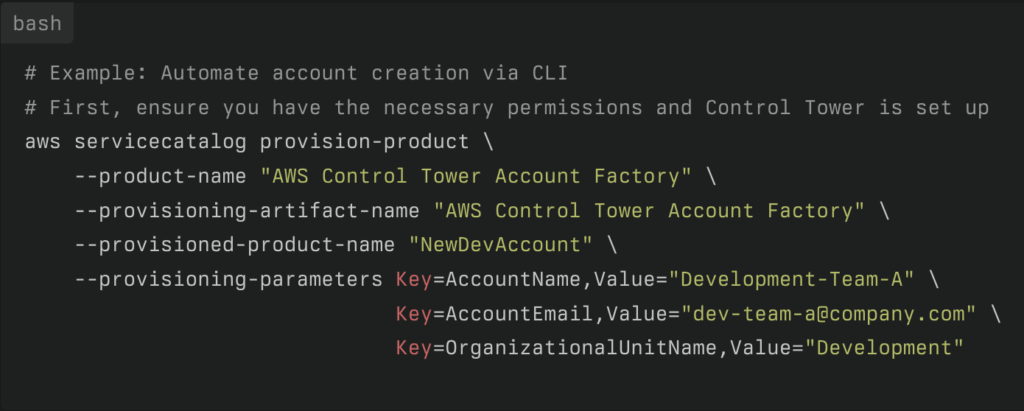
AWS Control Tower’s Account Factory automates account creation using AWS Service Catalog under the hood. This means:
- Template-driven provisioning: Every new account gets the same security baseline
- API-driven workflows: Integrate account creation into your CI/CD pipelines
- Automatic enrollment: New accounts are automatically registered with Control Tower guardrails
Now that you have your automated landing zone in place, it’s time to tackle the foundation of all cloud security: identity and access management.
Phase 2: Build a Strong Identity Foundation with Automation
| Goal | What “Good” Looks Like | AWS Services & Tools | Automation Layer |
| Centralized identity management | Single sign-on with MFA for all users | IAM Identity Center, IdP integration | Automated user provisioning |
| Least privilege access | Role-based permissions with regular reviews | IAM Access Analyzer, AWS-managed policies | Automated permission auditing |
| Secure credential management | No long-term static credentials | Cross-account roles, temporary credentials | Automated role assumption |
The Three Pillars of AWS Identity Security
- Retire the root account: Protect it with MFA and store the credentials in a vault; never use it for daily tasks.
- Centralize identities with automation: Connect Okta, Azure AD, or another IdP to IAM Identity Center and enforce MFA for every human user. Control Tower automatically configures this during landing zone setup.
- Least privilege by default:
- Start with AWS-managed job-function policies only when needed
- Automate permission reviews: Run IAM Access Analyzer continuously to flag overly broad permissions
Success Metrics for Phase 2
- MFA Adoption rate: 100% for all human users with enforced policy and regular compliance audits.
- Permission violations: < 5 per month across all accounts with real-time monitoring and automated remediation
- Identity governance compliance: 100% adherence to role-based access control (RBAC) principles
With identity management automated, let’s focus on protecting your most valuable asset: your data.
Phase 3: Protect Data Everywhere with Automated Controls
| Data State | Action | AWS Capability | Automation Layer |
| At rest | Encrypt everything; CMKs for regulated data | S3 Default Encryption, RDS Encryption, KMS | Control Tower guardrails enforce encryption |
| In transit | Enforce TLS 1.2+; HTTPS-only CloudFront | ACM, CloudFront security policies | SCPs prevent unencrypted connections |
| In use | Mask or tokenize PII before analytics | Macie, DynamoDB S2S Encryption, custom Lambda | Automated data classification workflows |
Common Pitfalls and How to Avoid Them
Pitfall: Assuming default encryption settings are sufficient
Solution: Implement organization-wide encryption policies through SCPs
Pitfall: Forgetting about data in transit between services
Solution: Use VPC endpoints and enforce TLS through guardrails
Now that your data is protected, let’s build the detection and response capabilities that will keep you ahead of threats.
Phase 4: Detect, Respond, and Automate at Scale
| Goal | What “Good” Looks Like | AWS Services & Tools | Automation Layer |
| Threat detection | Real-time monitoring across all accounts | GuardDuty, Security Hub | Organization-wide deployment |
| Centralized visibility | Single pane of glass for security events | CloudTrail, VPC Flow Logs, EventBridge | Automated log aggregation |
| Incident response | Automated containment and notification | Lambda, Systems Manager | Cross-account remediation |
The Three Layers of Detection
- Native threat detection with centralized management
- GuardDuty in all regions & accounts (Control Tower can enable this organization-wide)
- Security Hub with the AWS Foundational Security Best Practices standard across all accounts
- Centralized monitoring through Organizations
Stream CloudTrail, VPC Flow Logs, and GuardDuty findings to the Log Archive account; alert on root logins, IAM policy changes, and high-severity findings
- Automated remediation at scale
EventBridge rules → Lambda functions that isolate non-compliant resources across all accounts in your organization.
Automation Highlights
- Organization-wide deployment: Use Control Tower’s StackSets integration to deploy security tools across all accounts simultaneously
- Centralized alerting: All security events flow to the Audit account for unified monitoring
- Automated response: Cross-account Lambda functions can quarantine resources in any member account
Success Metrics for Phase 4
- Mean time to detection: < 30 minutes for critical threats with basic CloudWatch alarms and GuardDuty notifications
- Mean time to response: < 2 hours for high-severity incidents with manual investigation and documented runbooks
- False positive rate: < 15% for automated alerts as teams learn to tune detection rules
Security is never “done” – it requires continuous improvement and adaptation to new threats.
Phase 5: Continuous Security Evolution and Optimization
| Cadence | Activity | Outcome | Automation Component |
| Quarterly | Well-ArchitectedSecurity Pillarreview | Track progress vs. AWS best practices | Control Tower compliance dashboard |
| Monthly | IAM permissions & key-rotation audit | Remove unused access, shorten key lifetimes | Automated Access Analyzer reports |
| Bi-annual | Incident-response “game day” | Validate runbooks, cut mean-time-to-recover | Automated playbook execution |
| Continuous | Drift detection and remediation | Maintain security posture automatically | Control Tower drift detection APIs |
Automation Focus Areas
- Continuous compliance monitoring: Control Tower’s detective guardrails run 24/7 across all accounts
- Automated drift remediation: When accounts drift from baseline, Control Tower can automatically re-apply configurations
- Self-healing infrastructure: Combine Control Tower with AWS Systems Manager for automated patching and configuration management
Automated Guardrail Management
Control Tower’s APIs now allow you to programmatically manage guardrails across your organization:
- Enable/disable controls based on compliance requirements
- Customize detective controls for your specific use cases
- Automate control assignment to new OUs as they’re created
Cross-Account Automation
With AWS Organizations and Control Tower working together, you can:
- Deploy security tools to all accounts simultaneously using StackSets
- Centralize log collection from hundreds of accounts automatically
- Enforce policies across the entire organization through SCPs
Putting It All Together
Follow the phases in order but iterate—security is never “done.” Most teams can complete Phases 1–3 within 60 days, then mature their detection and response capabilities over the next two quarters. The key difference with this approach is that automation is built in from the start, not added later.
Remember the Four Pillars:
- Automate first: every manual step today is tomorrow’s breach window
- Guardrails over gates: preventive controls that keep dev velocity high win hearts and audits
- Measure relentlessly: Control Tower’s compliance dashboard is your yardstick, so use it
- Scale through orchestration: AWS Organizations + Control Tower handle the complexity so you can focus on business value
The beauty of this approach is that as your organization grows from 10 accounts to 100+, the security and governance overhead stays manageable because it’s automated from the foundation up.
Ready to Get Started?
Building a secure AWS foundation doesn’t have to be overwhelming. Start with Phase 1 this week, and you’ll have a solid foundation in place within 60 days.
Need help implementing these recommendations? The WEI team has helped dozens of organizations build secure, scalable AWS environments. Contact us to discuss your specific requirements.
Questions about Control Tower guardrails, Organizations SCPs, or automated account provisioning?
Coming up next: Part 3 of our series covers Azure Security Blueprints and Microsoft’s five-pillar security model. Subscribe to stay updated!